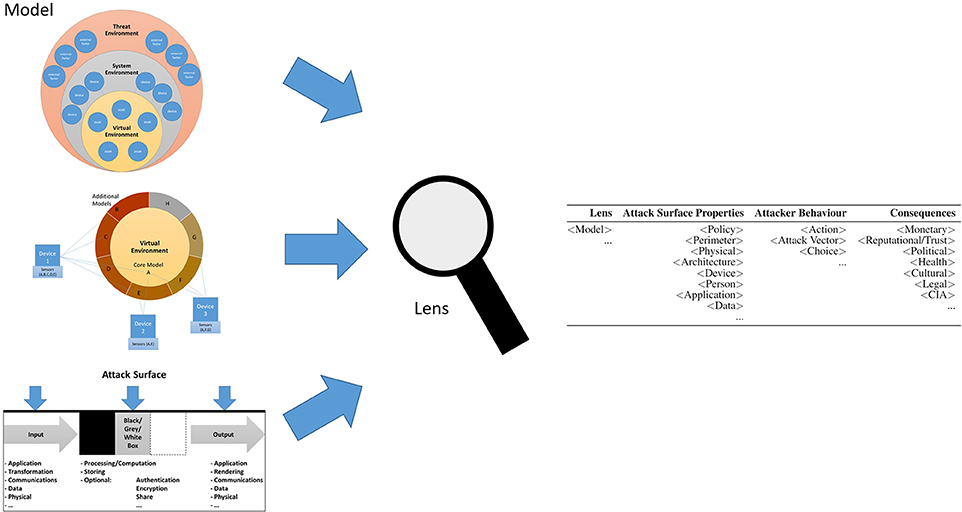
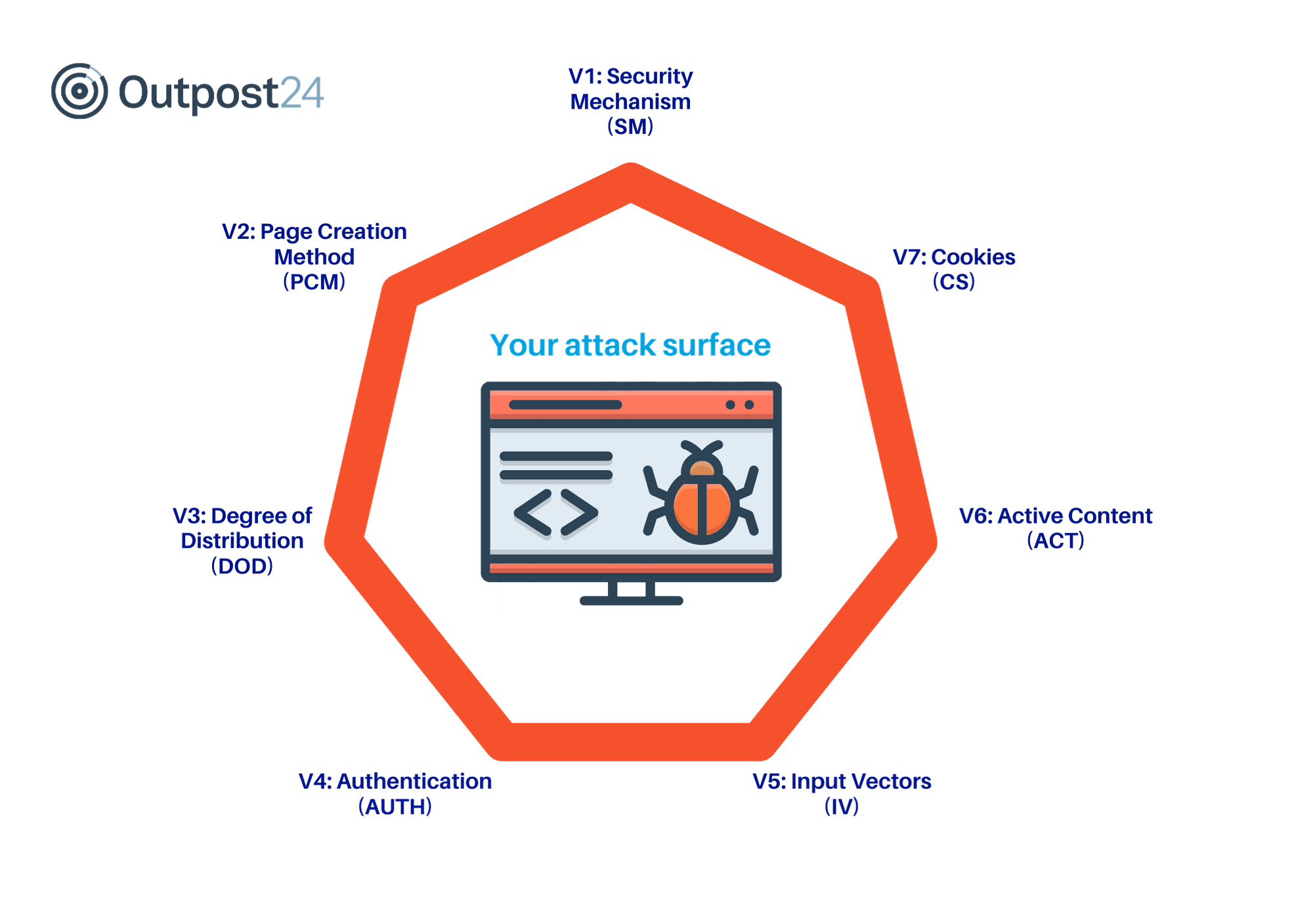
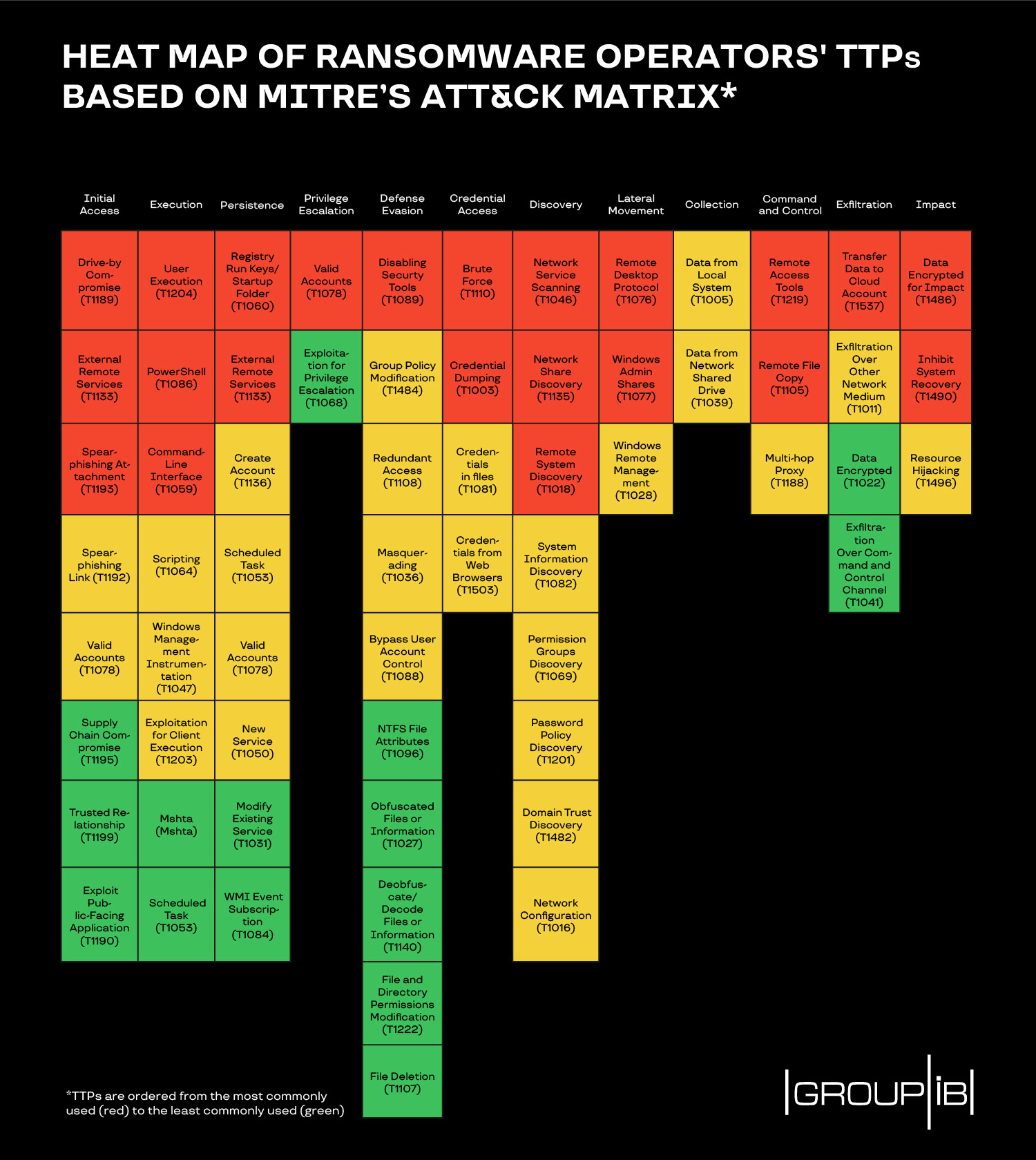
Complete Attack Vector and its relation with HAV, TAV and the business... | Download Scientific Diagram

Buy Identity Attack Vectors: Implementing an Effective Identity and Access Management Solution Book Online at Low Prices in India | Identity Attack Vectors: Implementing an Effective Identity and Access Management Solution Reviews

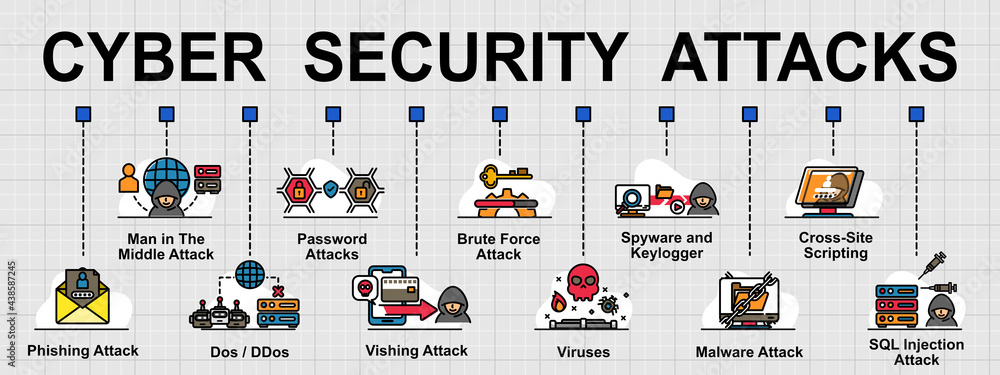
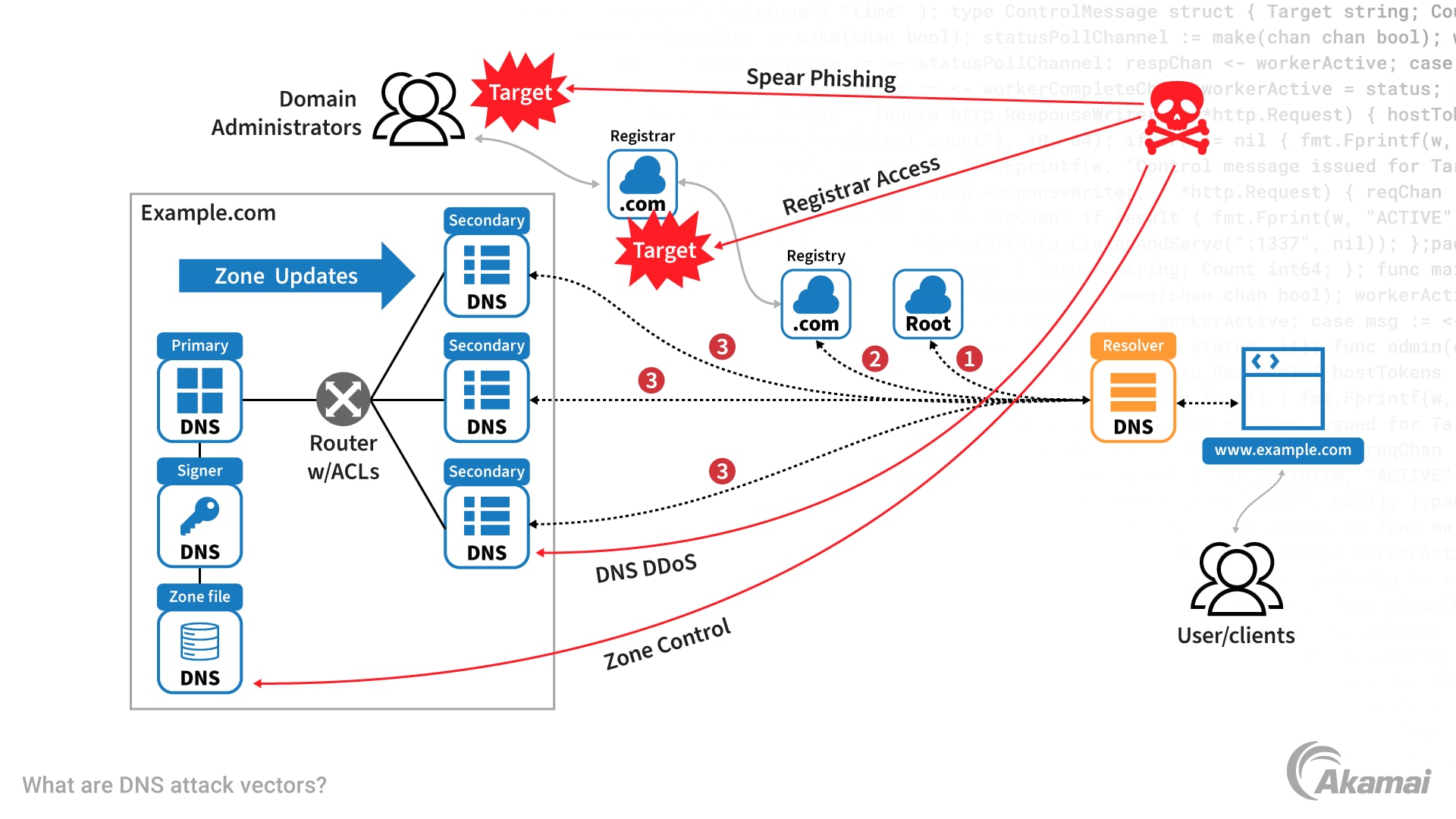
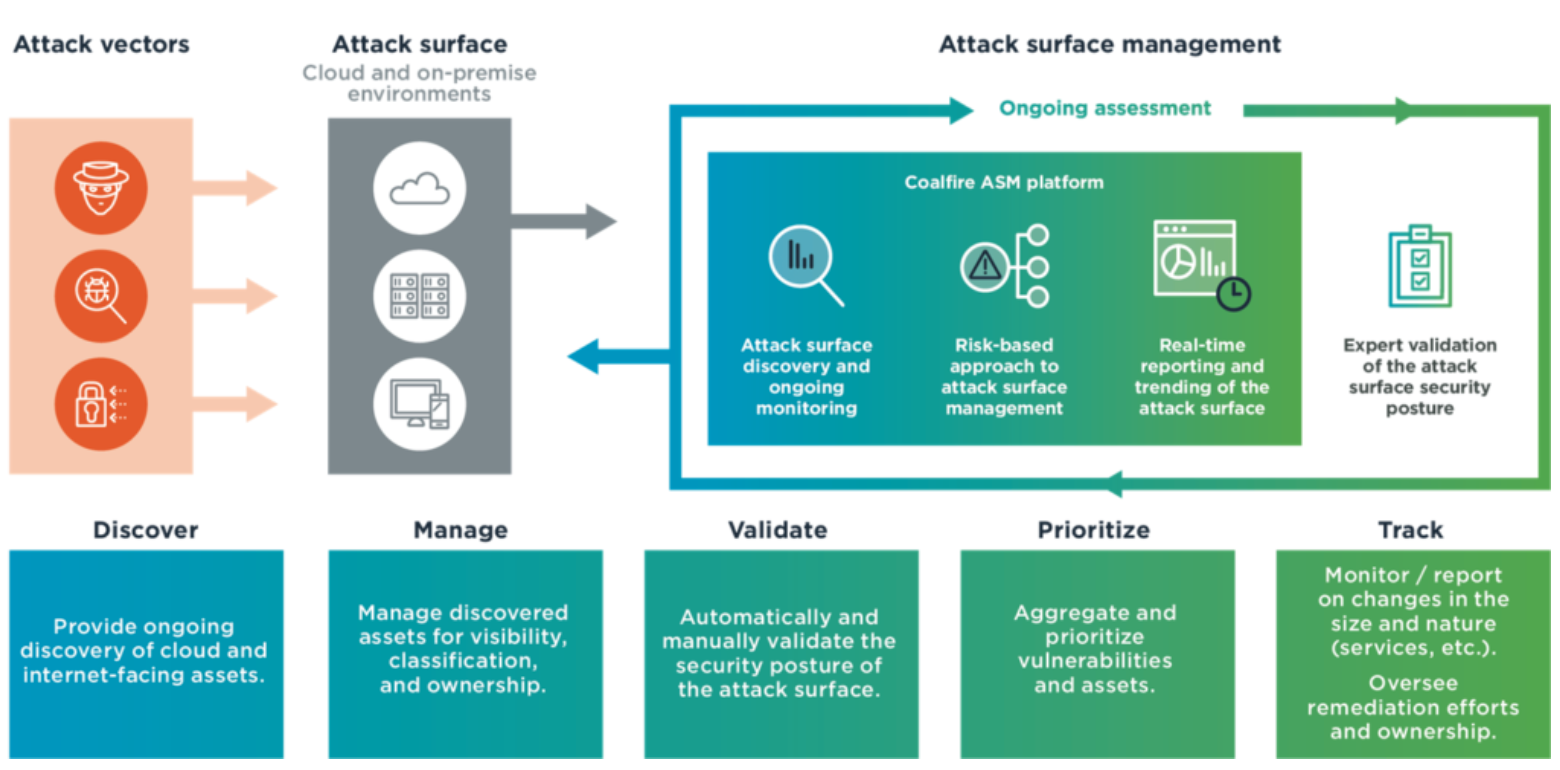
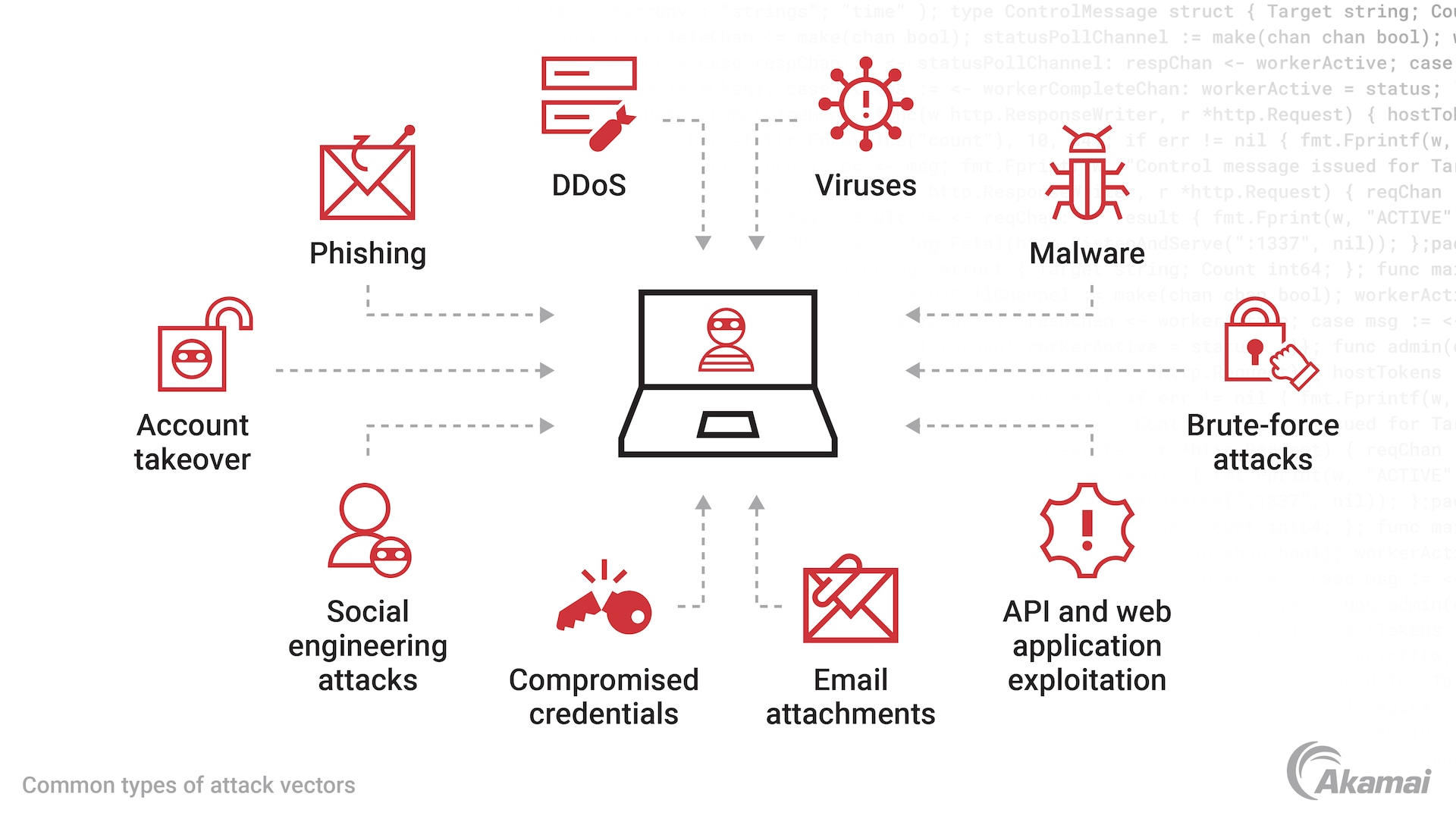
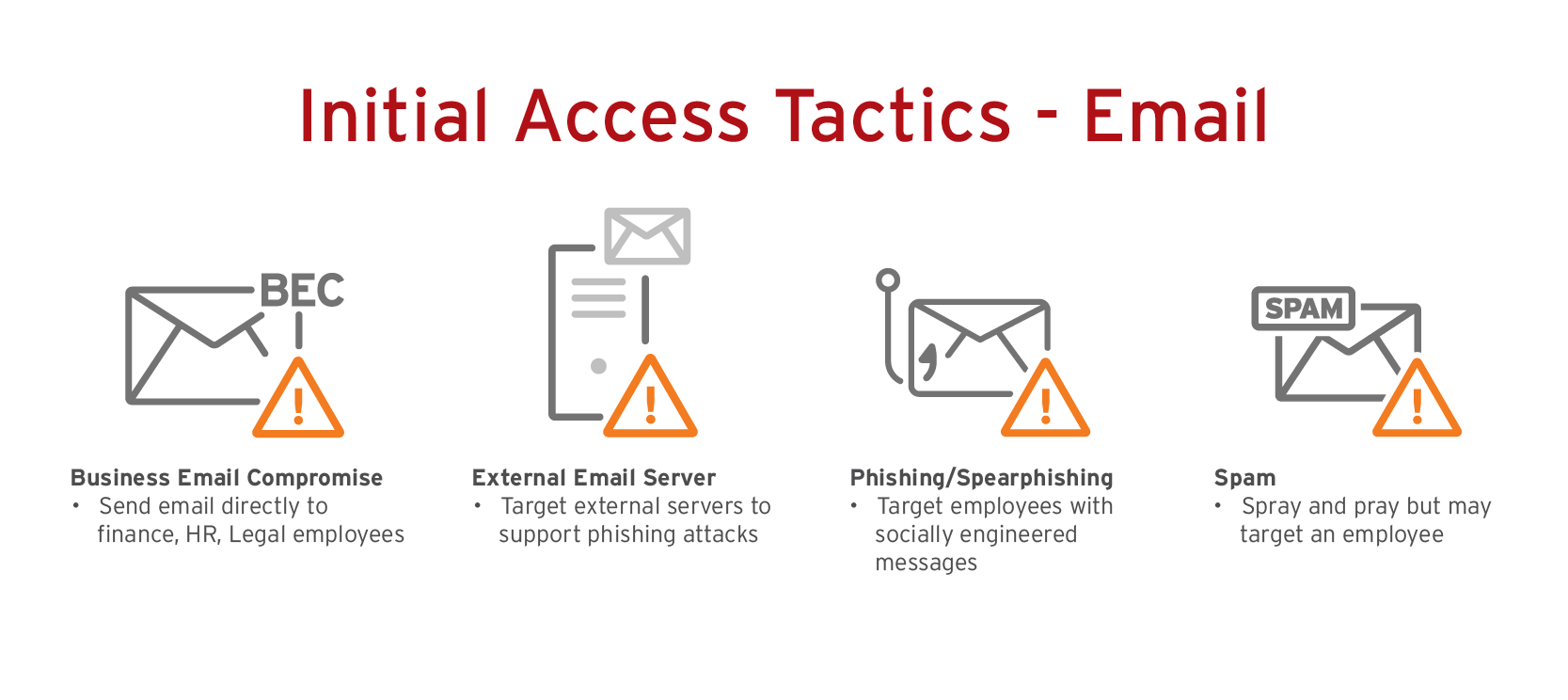
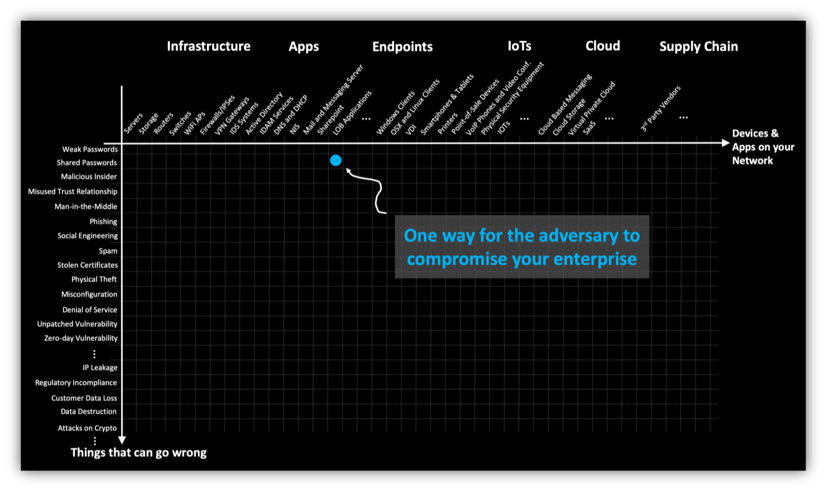
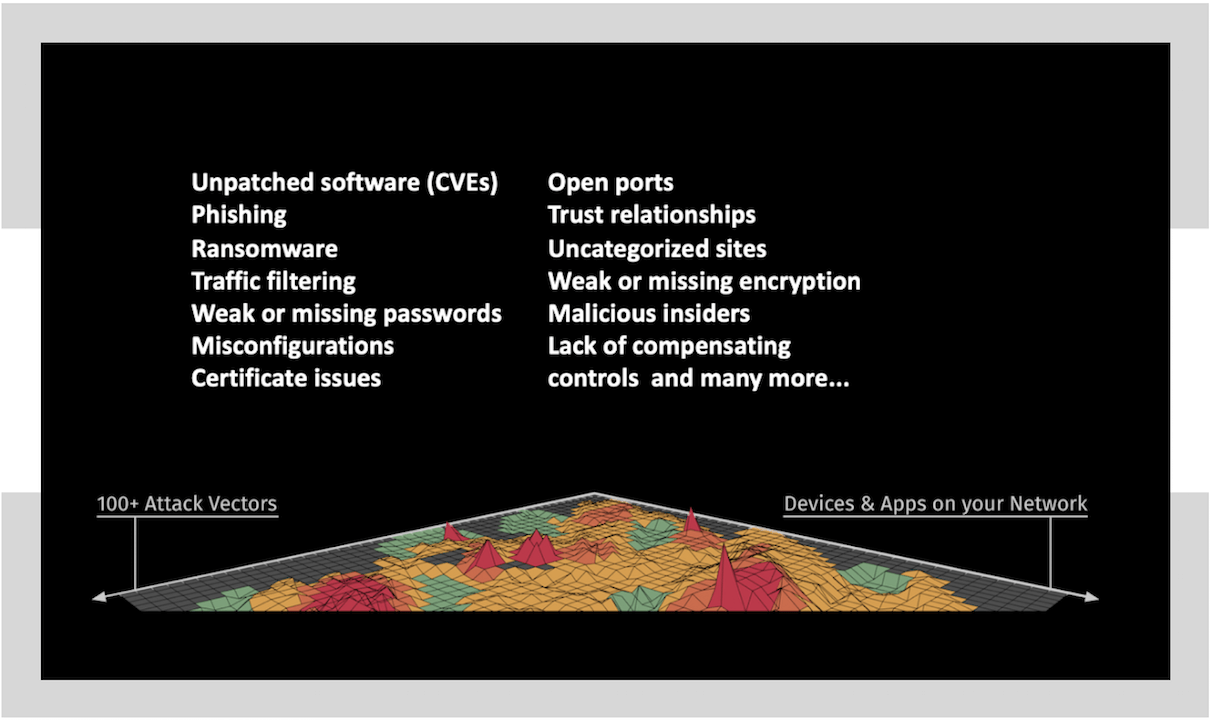
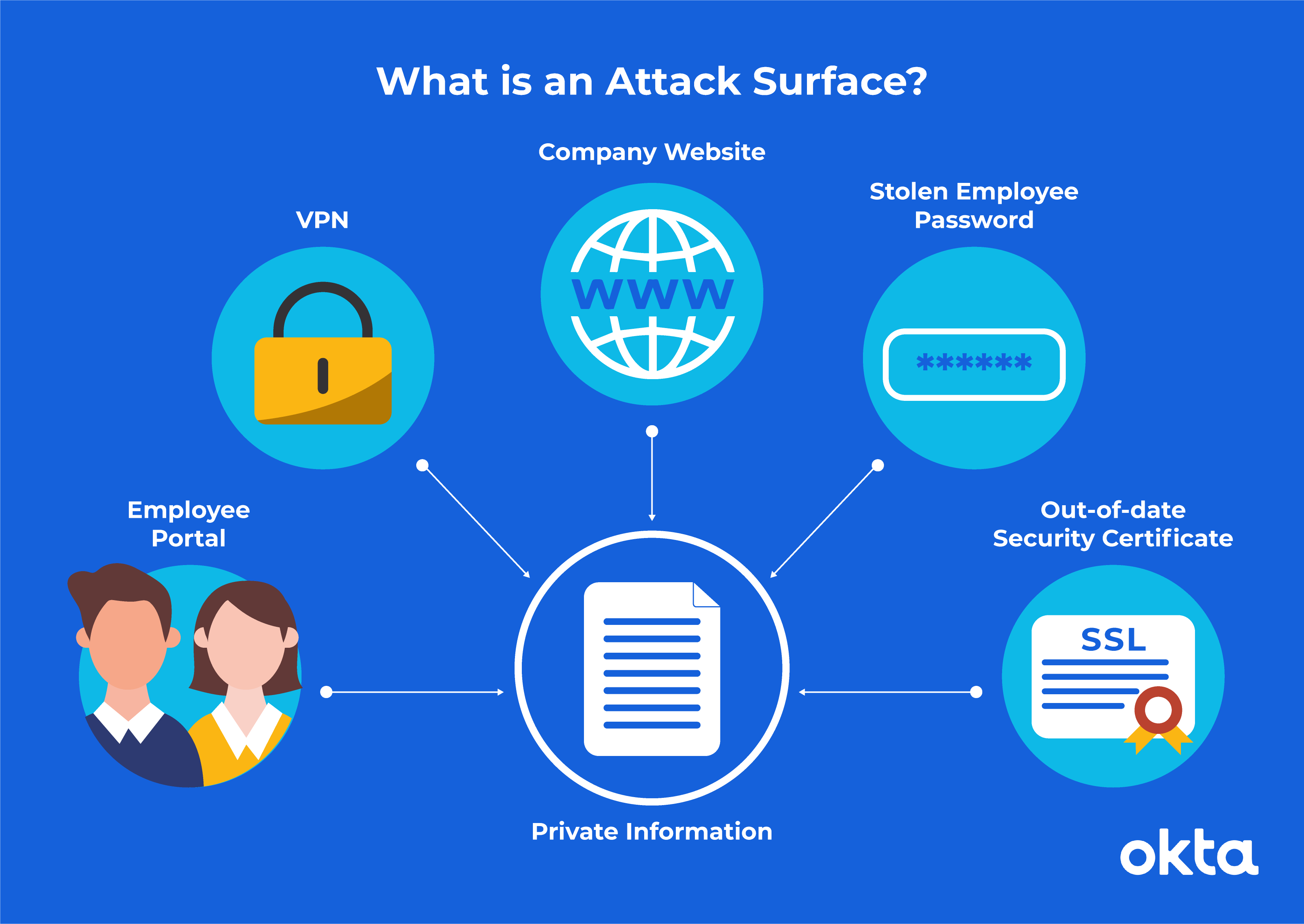
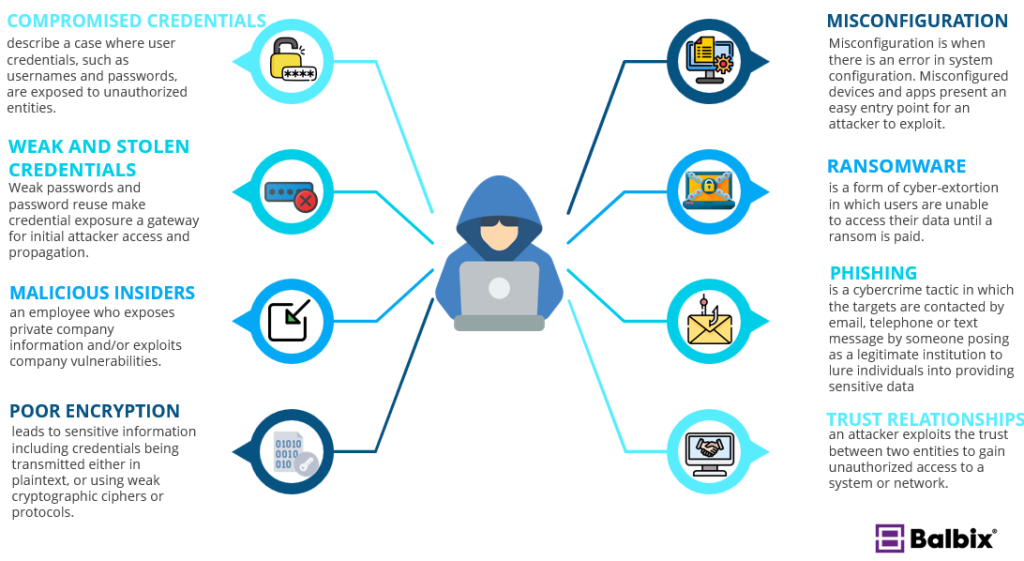
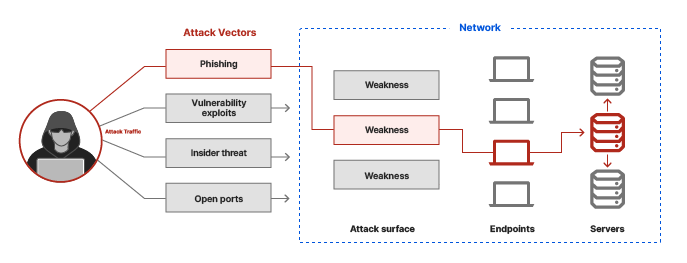
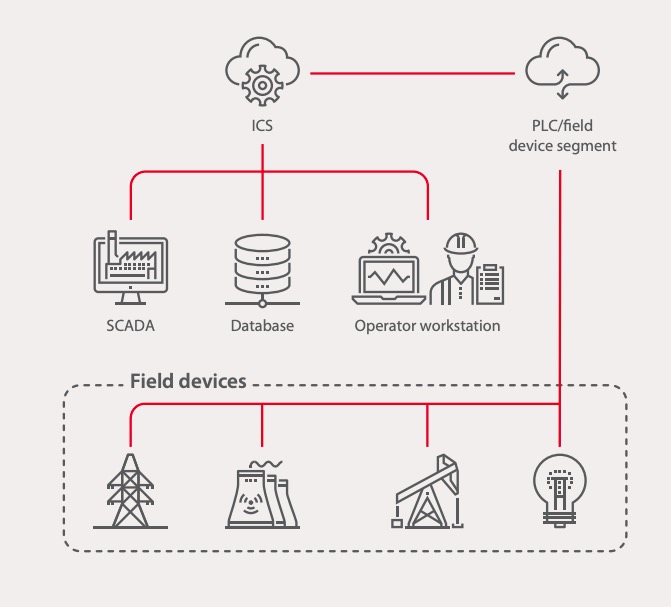
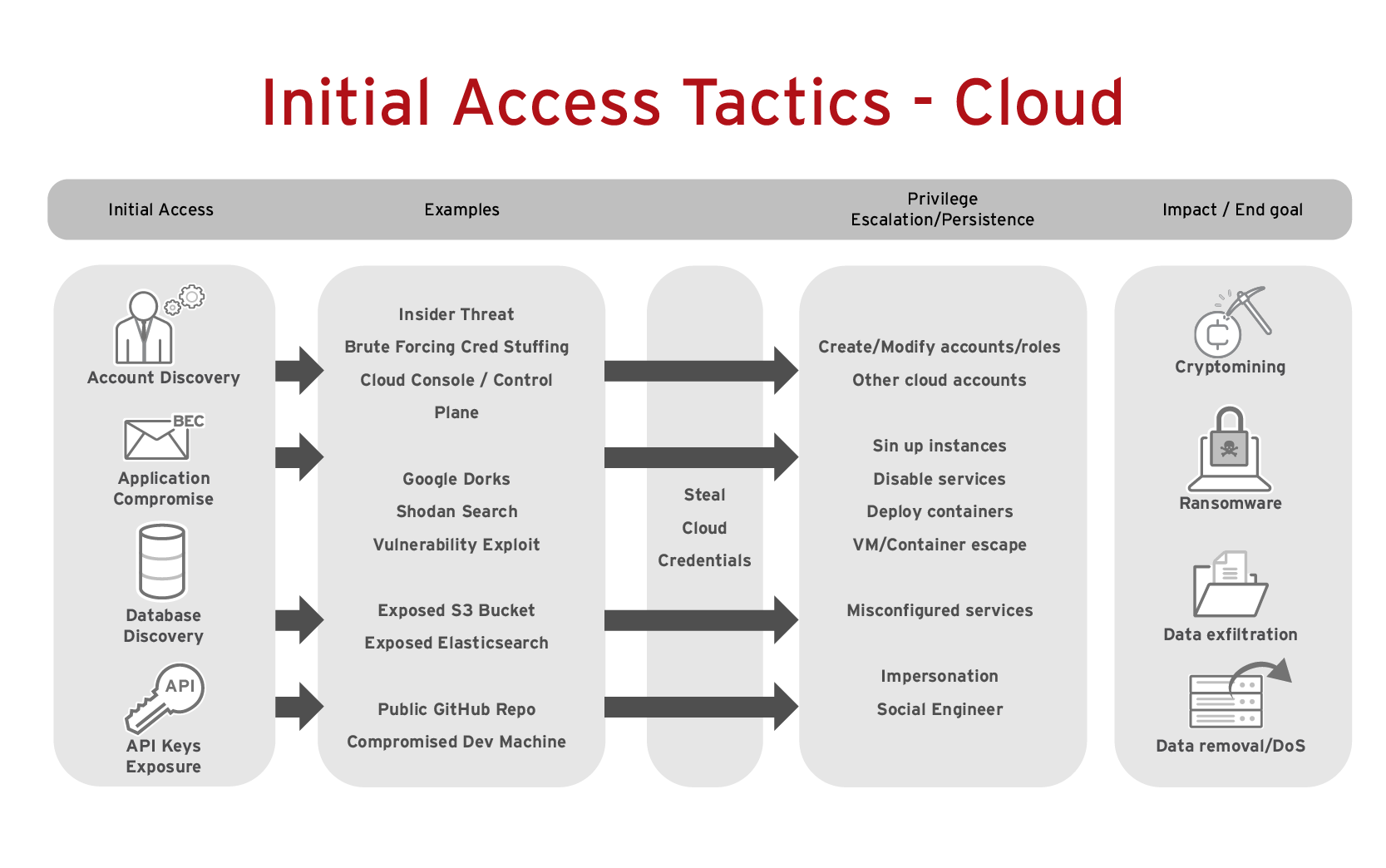
Cybersecurity Prism - What is an Attack Vector? In the context of information security, an attack vector is a specific path, method, or scenario that can be exploited by attackers to break