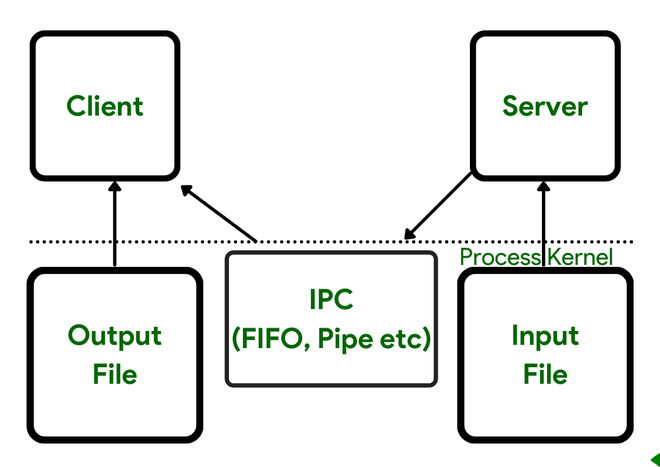
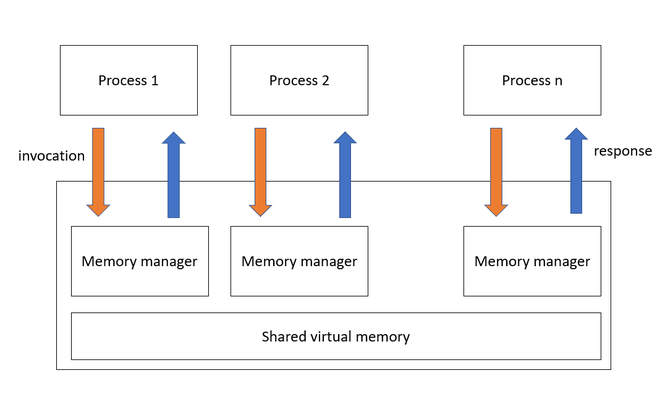
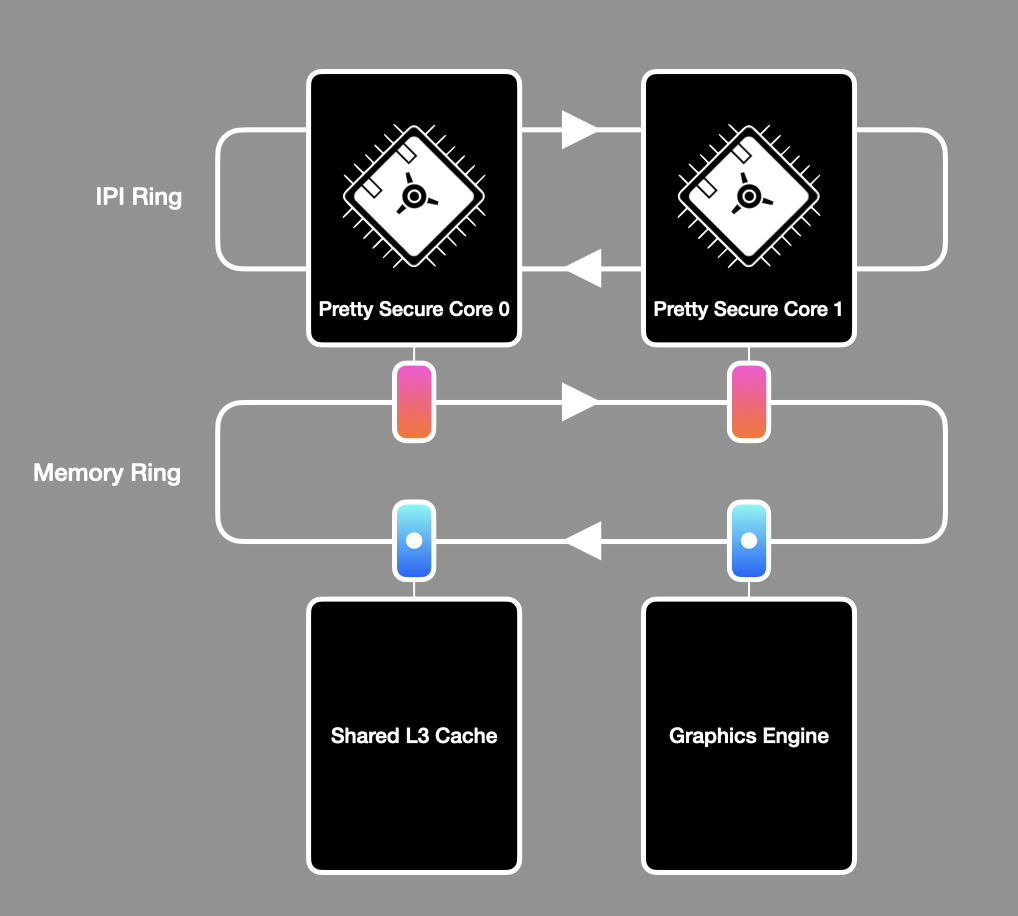
Citadel: Enclaves with Microarchitectural Isolation and Secure Shared Memory on a Speculative Out-of-Order Processor.
![PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b44880b53945fa95fd6a904f2854d6cf260b0897/5-Figure2-1.png)
PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar
![PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/b44880b53945fa95fd6a904f2854d6cf260b0897/3-Figure1-1.png)
PDF] SOTPM: Software One-Time Programmable Memory to Protect Shared Memory on ARM Trustzone | Semantic Scholar

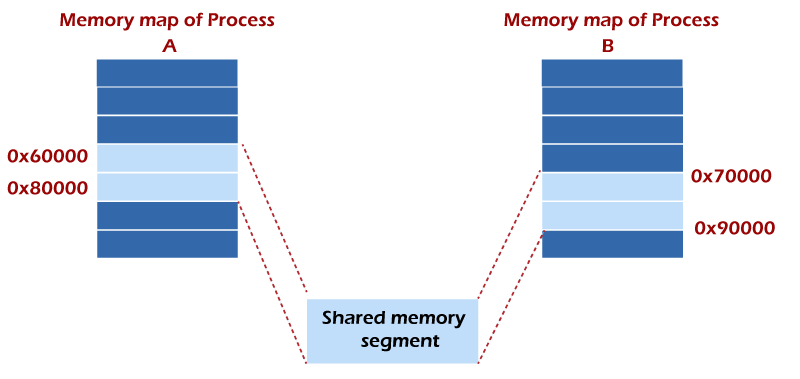



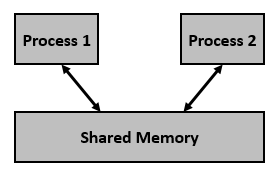

![PDF] SIVSHM: Secure Inter-VM Shared Memory | Semantic Scholar PDF] SIVSHM: Secure Inter-VM Shared Memory | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/772c20cd2e68bd005f848d9fca31bff415498fef/4-Figure1-1.png)