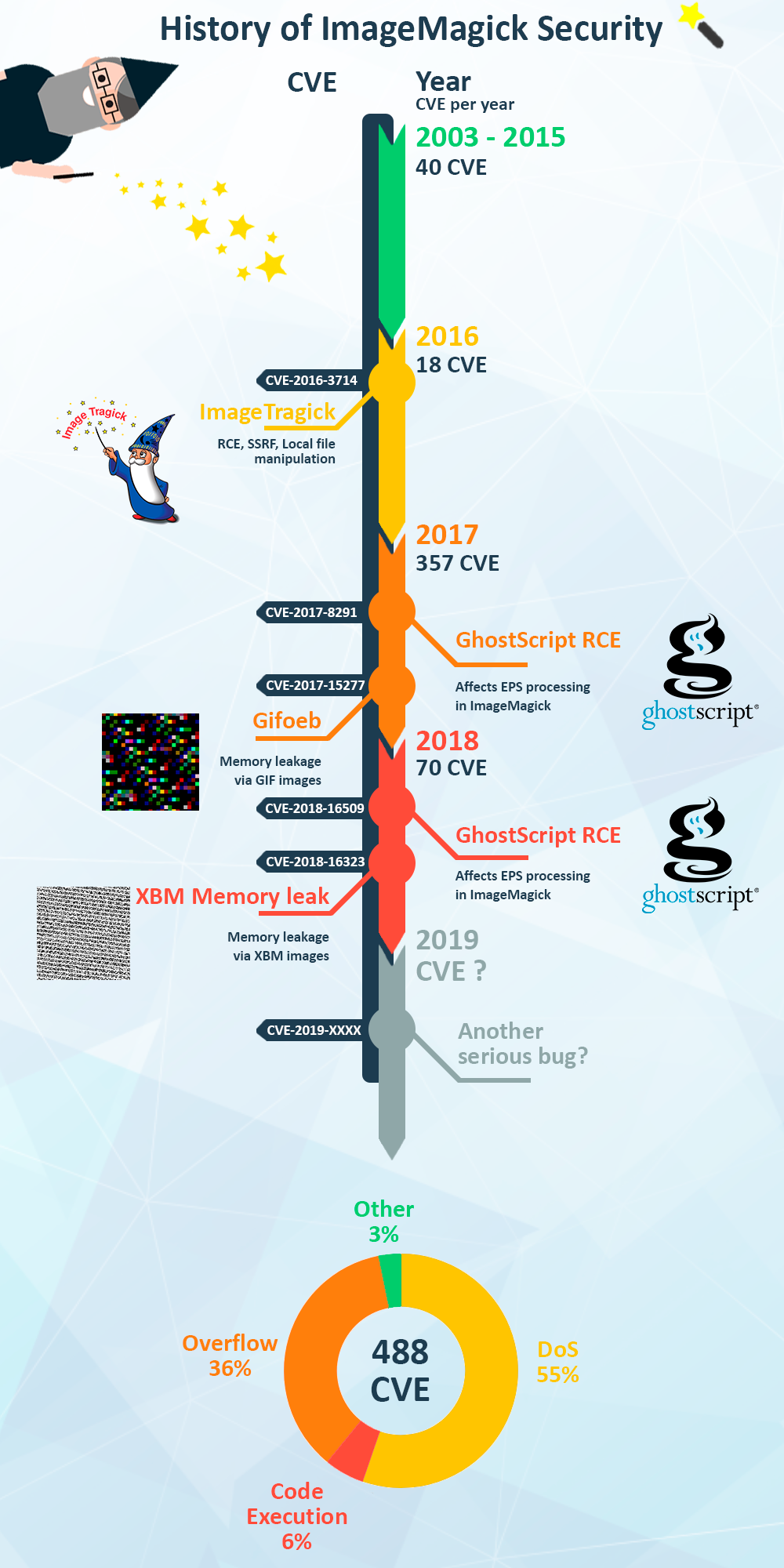
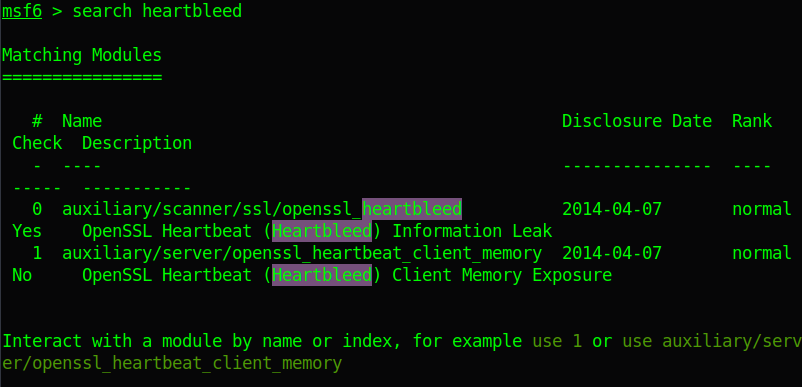
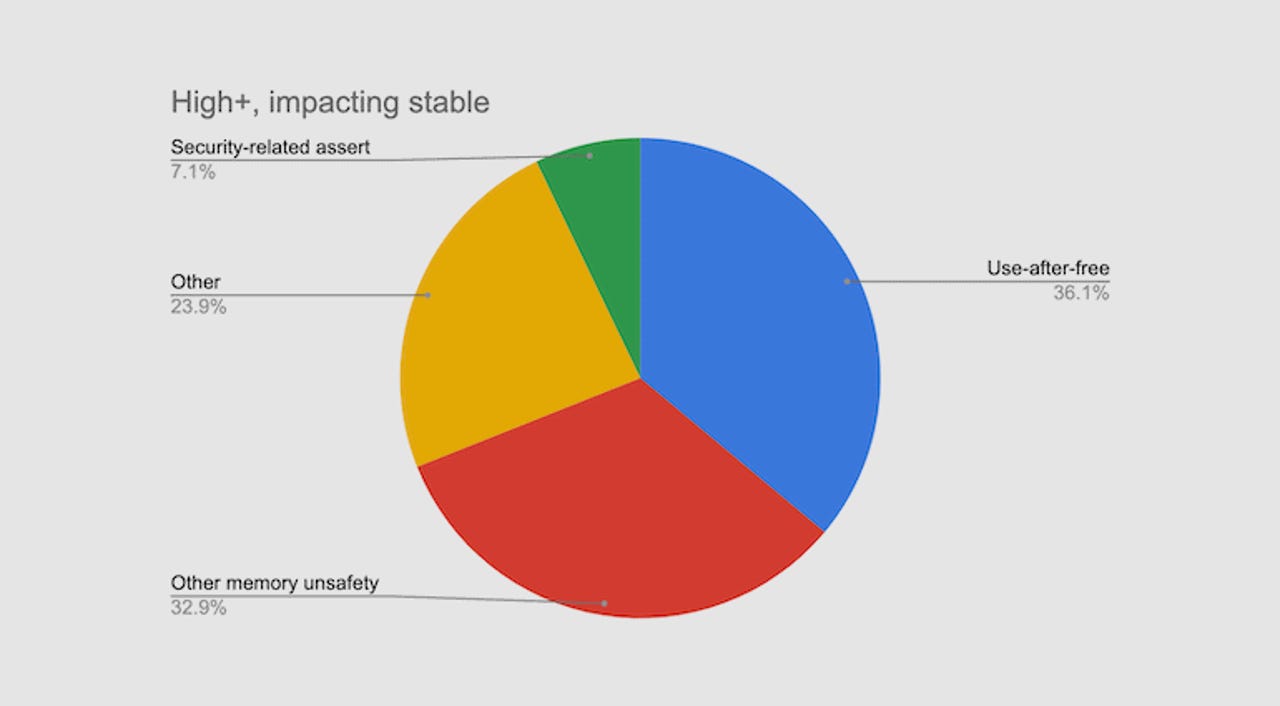
Part 6 — My Talk “The Evolution Of Exploiting Memory Vulnerabilities In Linux” | by Ofri Ouzan | Medium
Part 6 — My Talk “The Evolution Of Exploiting Memory Vulnerabilities In Linux” | by Ofri Ouzan | Medium
Part 6 — My Talk “The Evolution Of Exploiting Memory Vulnerabilities In Linux” | by Ofri Ouzan | Medium
Part 6 — My Talk “The Evolution Of Exploiting Memory Vulnerabilities In Linux” | by Ofri Ouzan | Medium

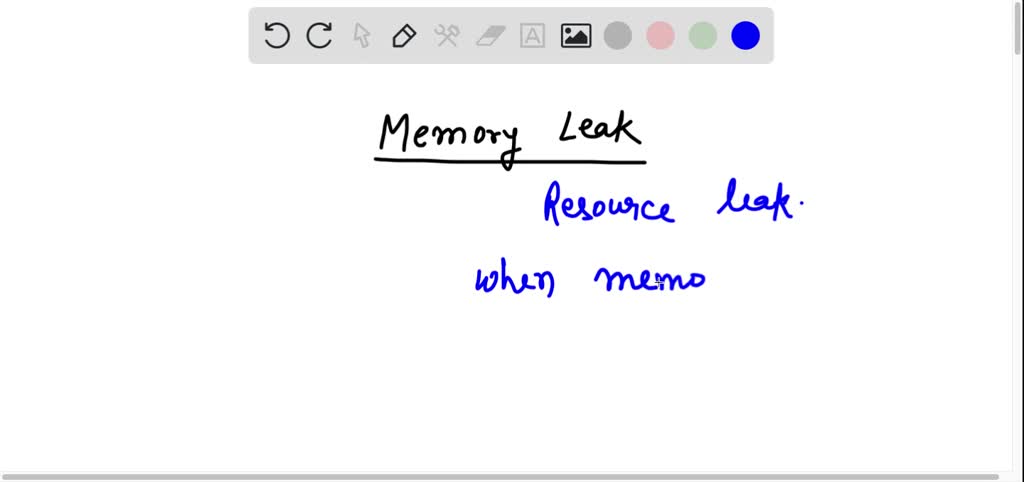
How memory leaks leave the door open for hackers and how Functional Programming can remedy that - Ada Beat