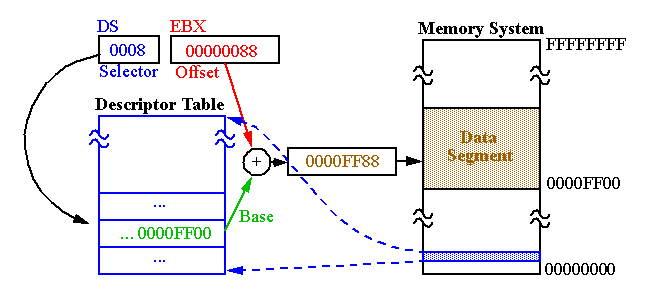
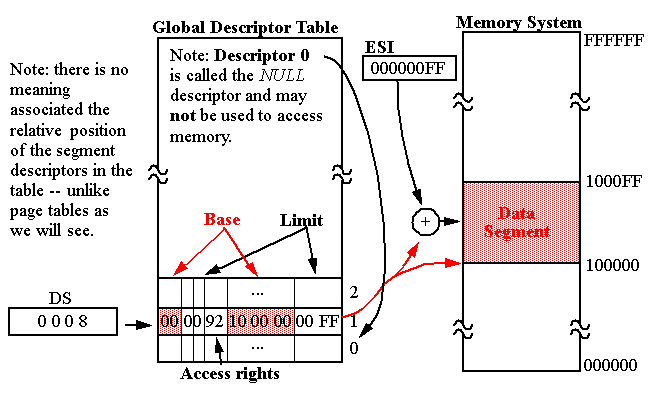
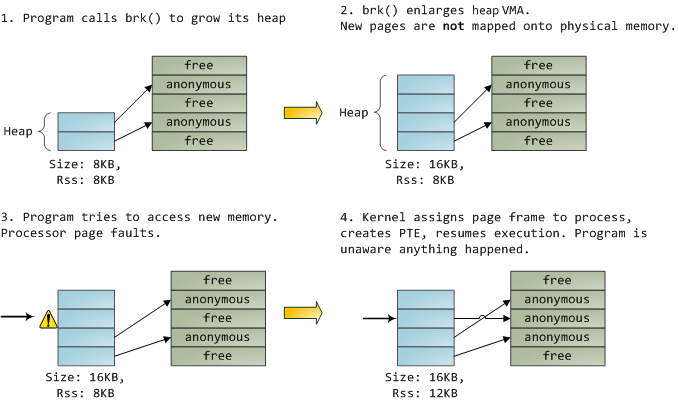
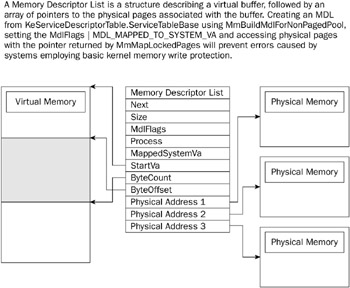
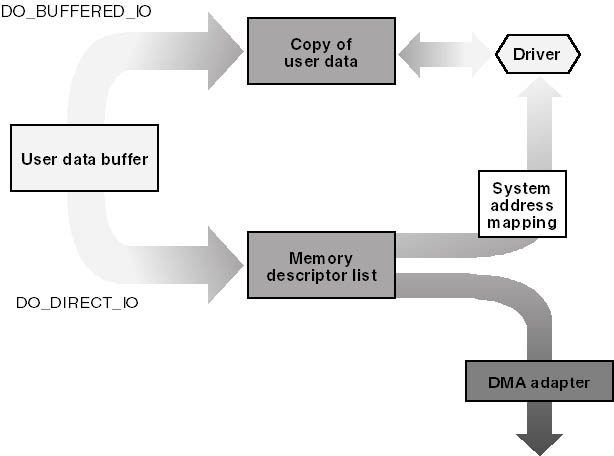
A look at memory issues Data-transfers must occur between system memory and the network interface controller. - ppt download
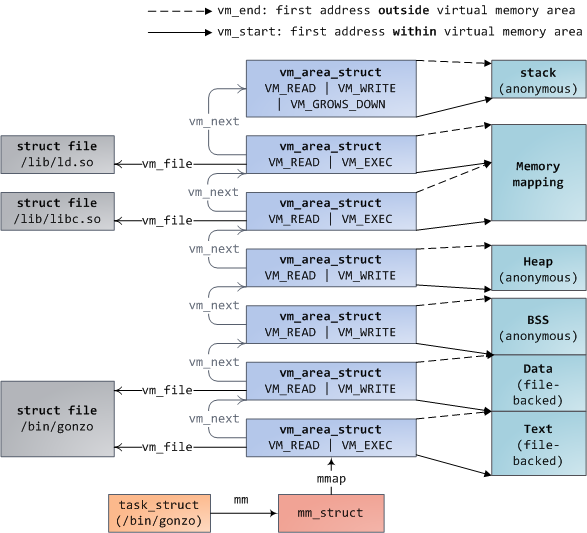
![Windows Process Internals: A few Concepts to know before jumping on Memory Forensics [Part 4] — Journey in to the Undocumented VAD Structures (Virtual Address Descriptors) | By Kirtar Oza - eForensics Windows Process Internals: A few Concepts to know before jumping on Memory Forensics [Part 4] — Journey in to the Undocumented VAD Structures (Virtual Address Descriptors) | By Kirtar Oza - eForensics](https://eforensicsmag.com/wp-content/uploads/2020/09/image8-1.png)
Windows Process Internals: A few Concepts to know before jumping on Memory Forensics [Part 4] — Journey in to the Undocumented VAD Structures (Virtual Address Descriptors) | By Kirtar Oza - eForensics

Electronics | Free Full-Text | Memory Layout Extraction and Verification Method for Reliable Physical Memory Acquisition

Match list and memory descriptor configuration for receiving message... | Download Scientific Diagram

Details of Memory Access Pattern's Regular/Irregular Memory Descriptor... | Download Scientific Diagram

A buffer descriptor queue consisting of three BDs located in the memory... | Download Scientific Diagram