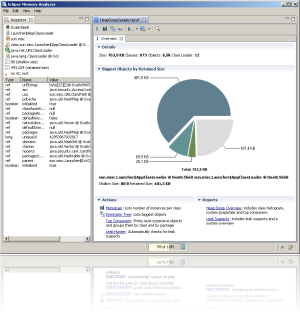
The Long Short-Term Memory analysis procedure. The resting-state fMRI... | Download Scientific Diagram

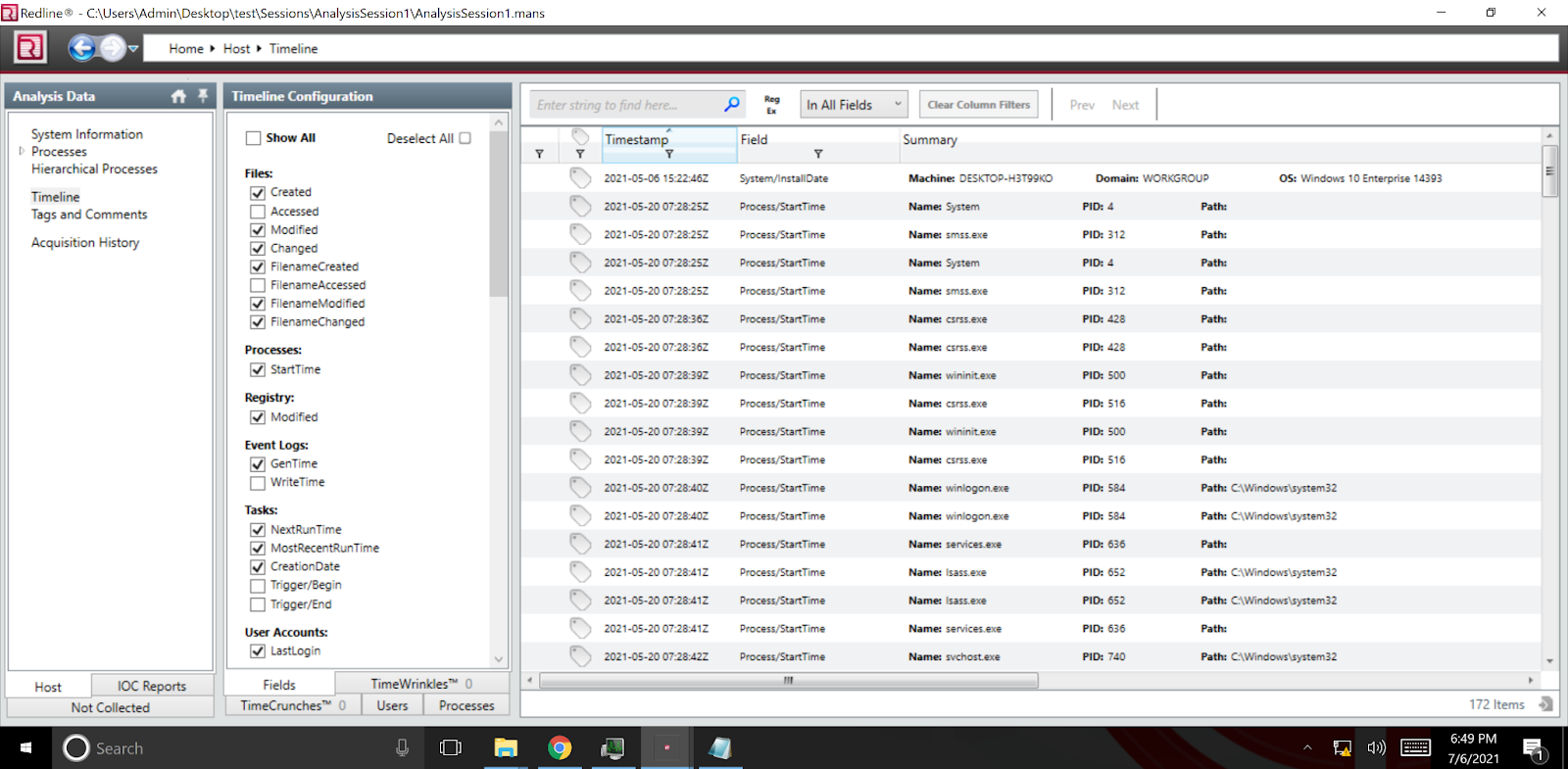
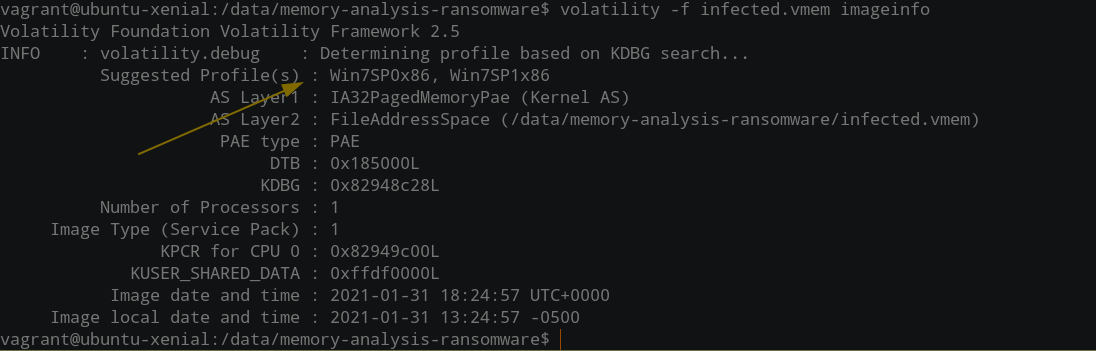
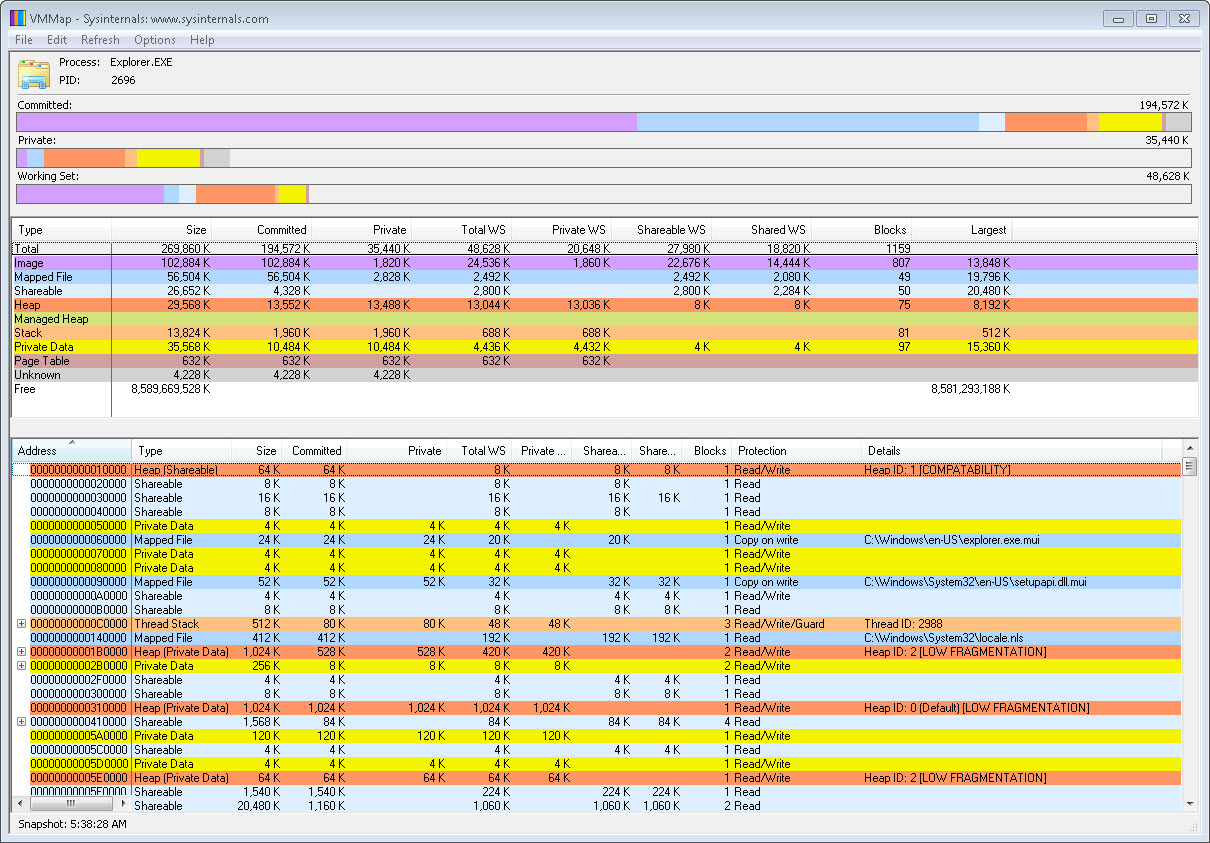
Incident Response and Threat Hunting with Redline:Power of Live Memory Analysis Part 1 | by Abel Sekibaala | Medium
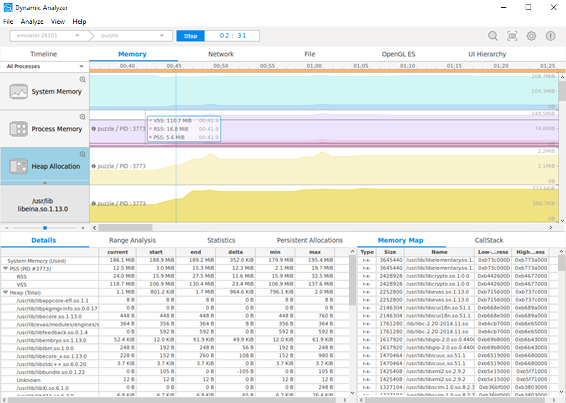
Full Memory Crash Dumps vs. Raw Dumps: Which Is Best for Memory Analysis for Incident Response ? - Magnet Forensics
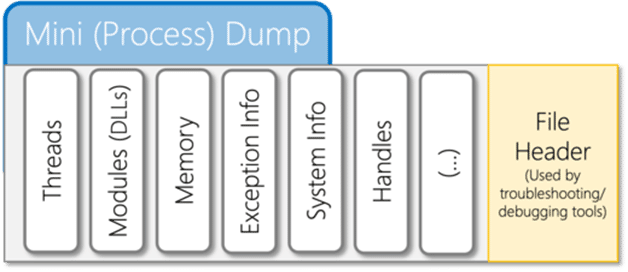
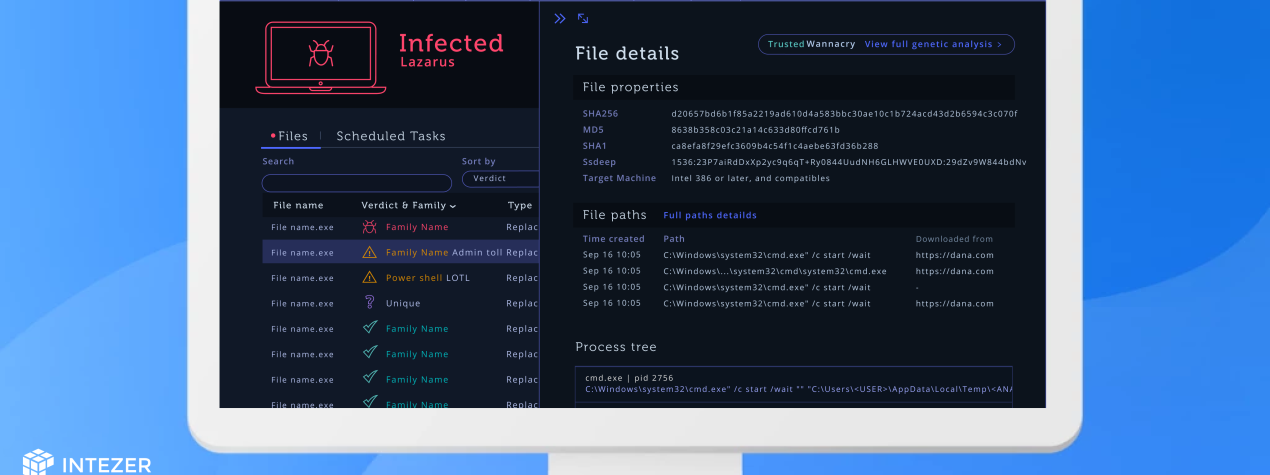

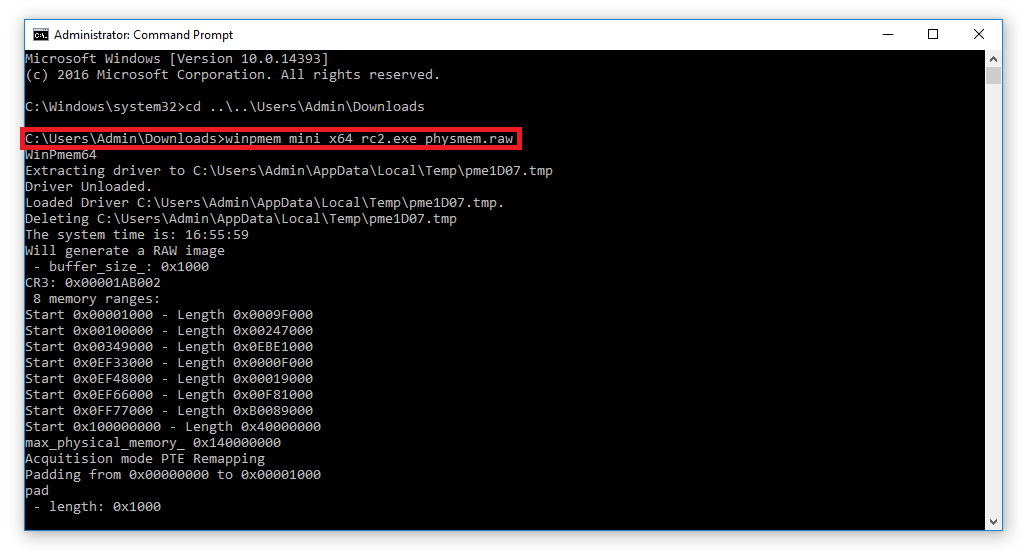
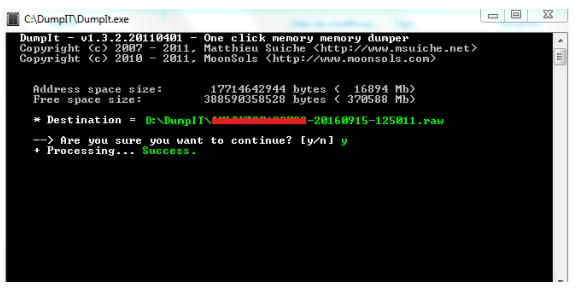



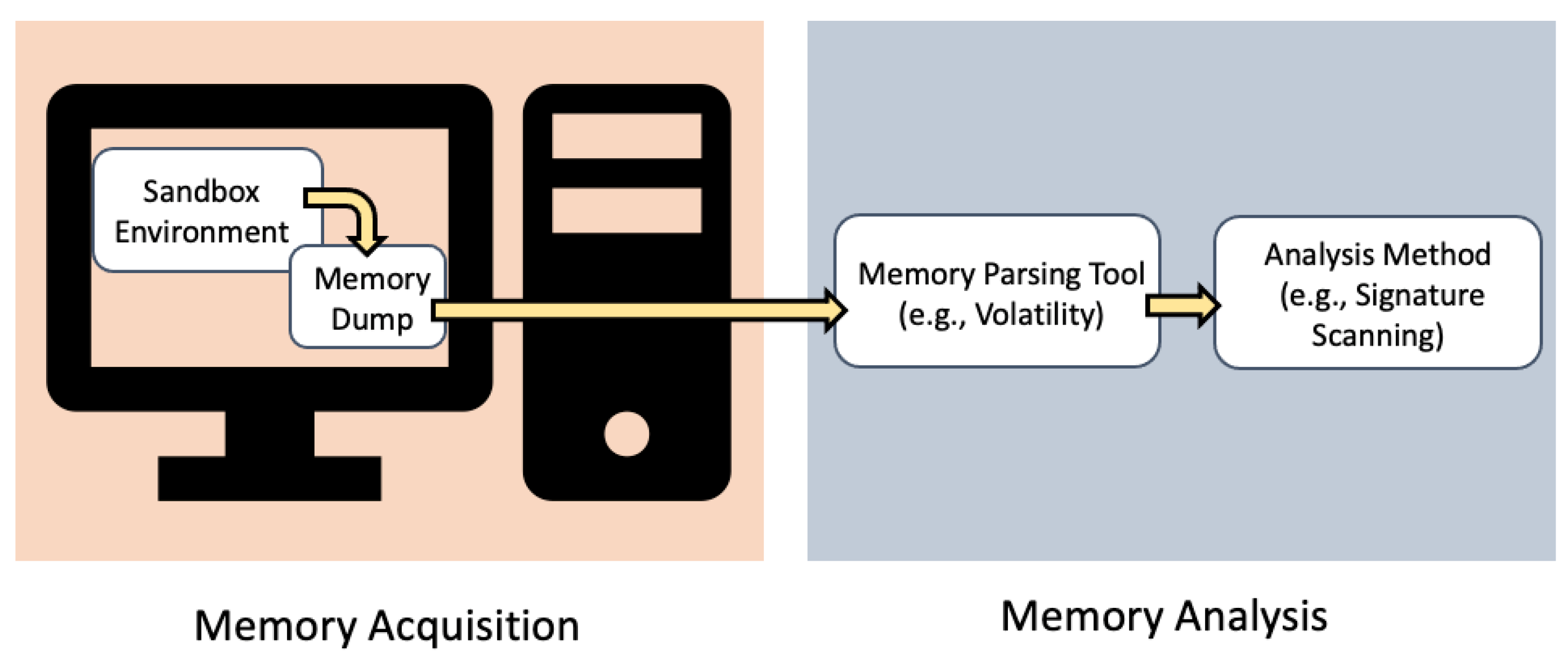
![PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar PDF] Memory Forensics: Review of Acquisition and Analysis Techniques | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5844da2c4456091748958bcc035ff8a52e6d8340/18-Figure1-1.png)