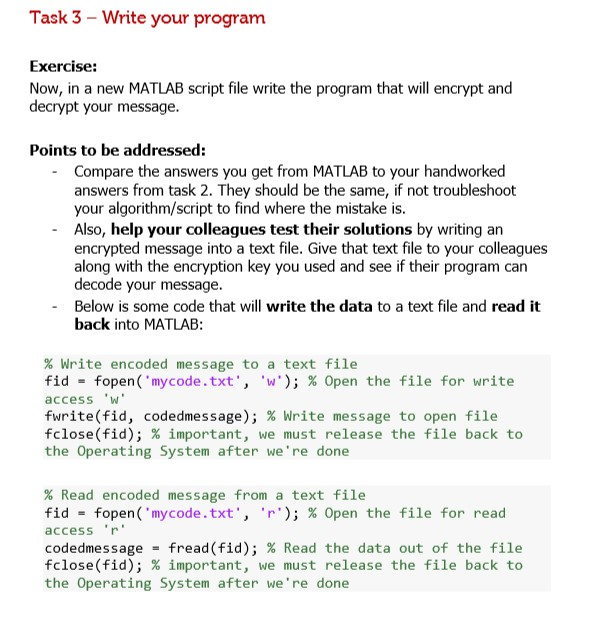
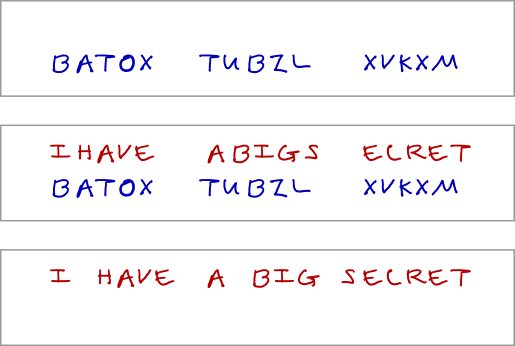
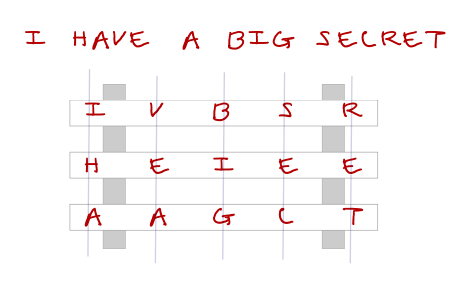
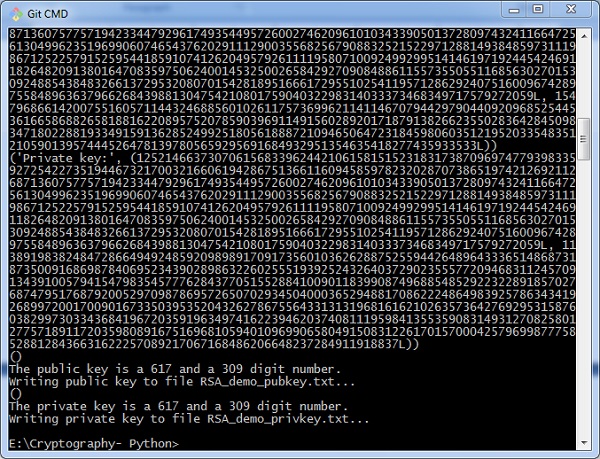
Developing the Art of Secret Writing across Borders: The Journey of Marie de Guise's Ciphers between France and Scotland

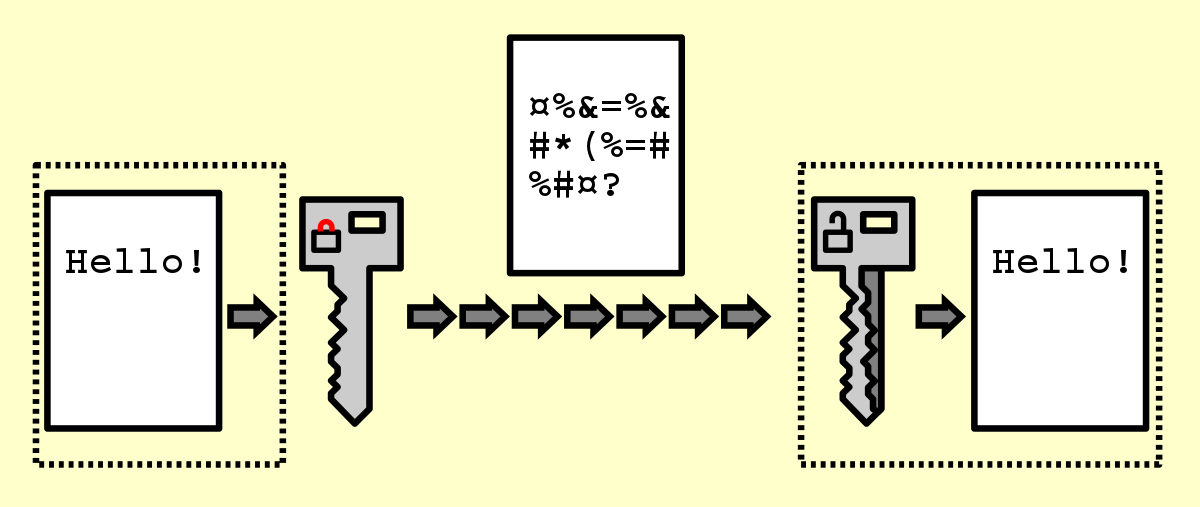
Writing Note Showing End To End Encryption System. Business Photo Showcasing Method Used for Securing Encrypted Data Stock Illustration - Illustration of encrypted, private: 135615730
Handwriting Text Writing Vpn Virtual Private Network. Concept Meaning Safe Encrypted Connection Over the Internet Stock Illustration - Illustration of computer, communication: 128725594

I need help deciphering encrypted writing I found under my doormat. I've been trying for hours on my own. : r/codes

Handwriting text writing End To End Encryption System. Concept meaning method used for securing encrypted data Blank Sheet of Bond Paper on Clipboard Stock Photo - Alamy

SOLVED: Question 1. In a transposition cipher, the order of the characters is changed to encrypt the message by writing the message in rows and then forming the encrypted message from the

Handwriting text writing Encrypted Folder. Concept meaning protect confidential data from attackers with access Clipboard holding blank paper sheet note binder pencil colored background, Art Print | Barewalls Posters & Prints | bwc71132704