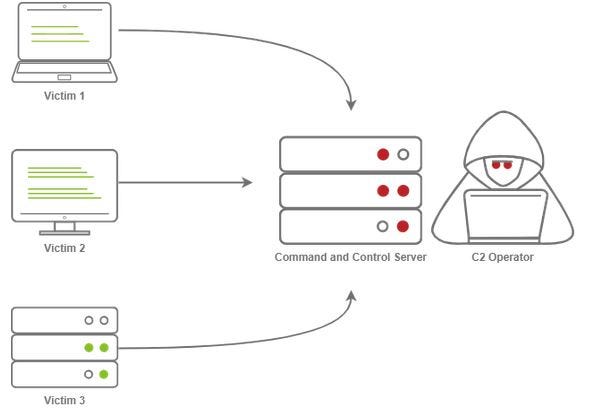
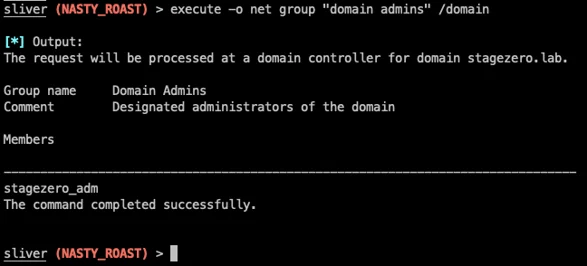
Stopping C2 communications in human-operated ransomware through network protection | Microsoft Security Blog

Stopping C2 communications in human-operated ransomware through network protection | Microsoft Security Blog
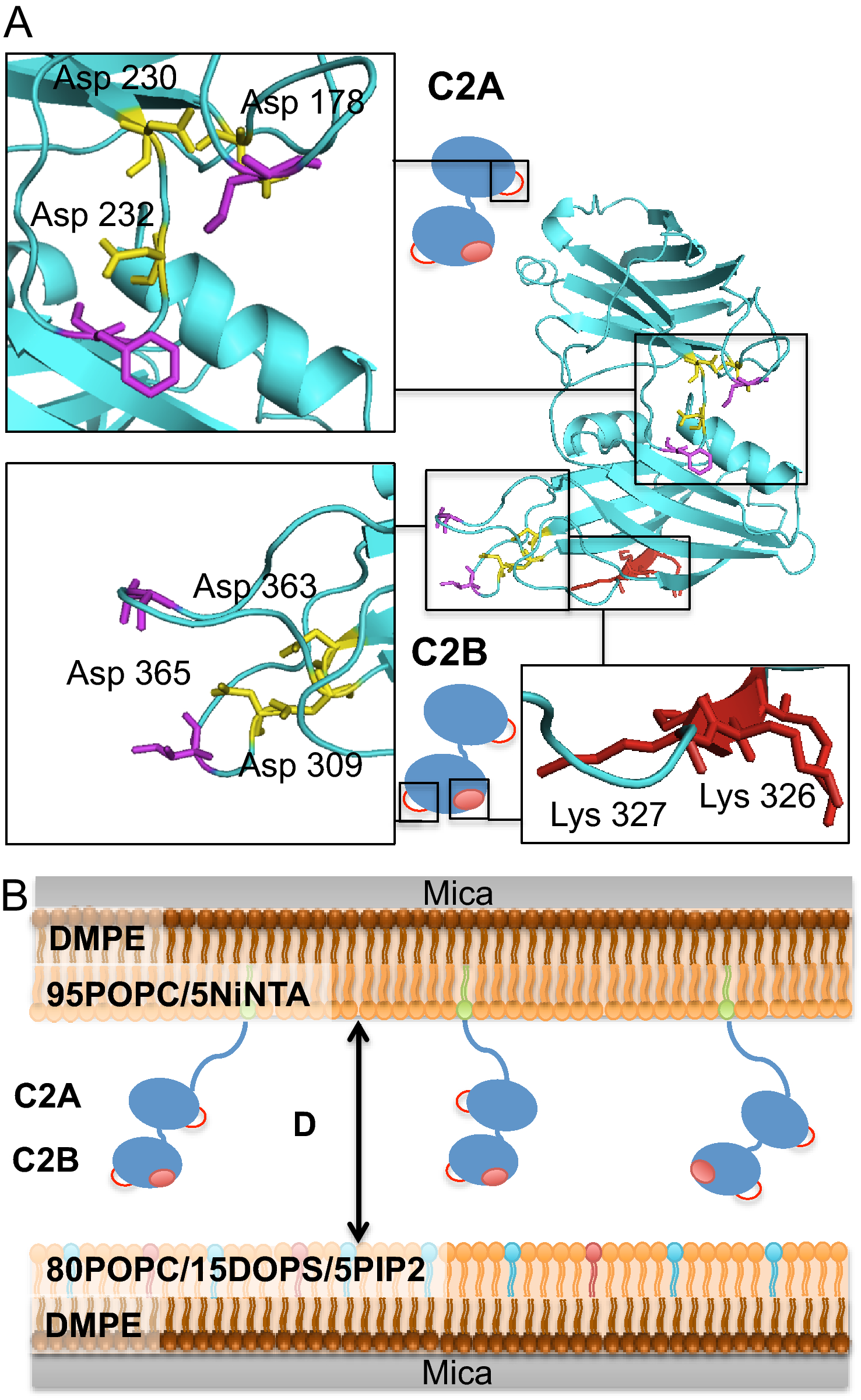
Synaptotagmin-1 membrane binding is driven by the C2B domain and assisted cooperatively by the C2A domain | Scientific Reports
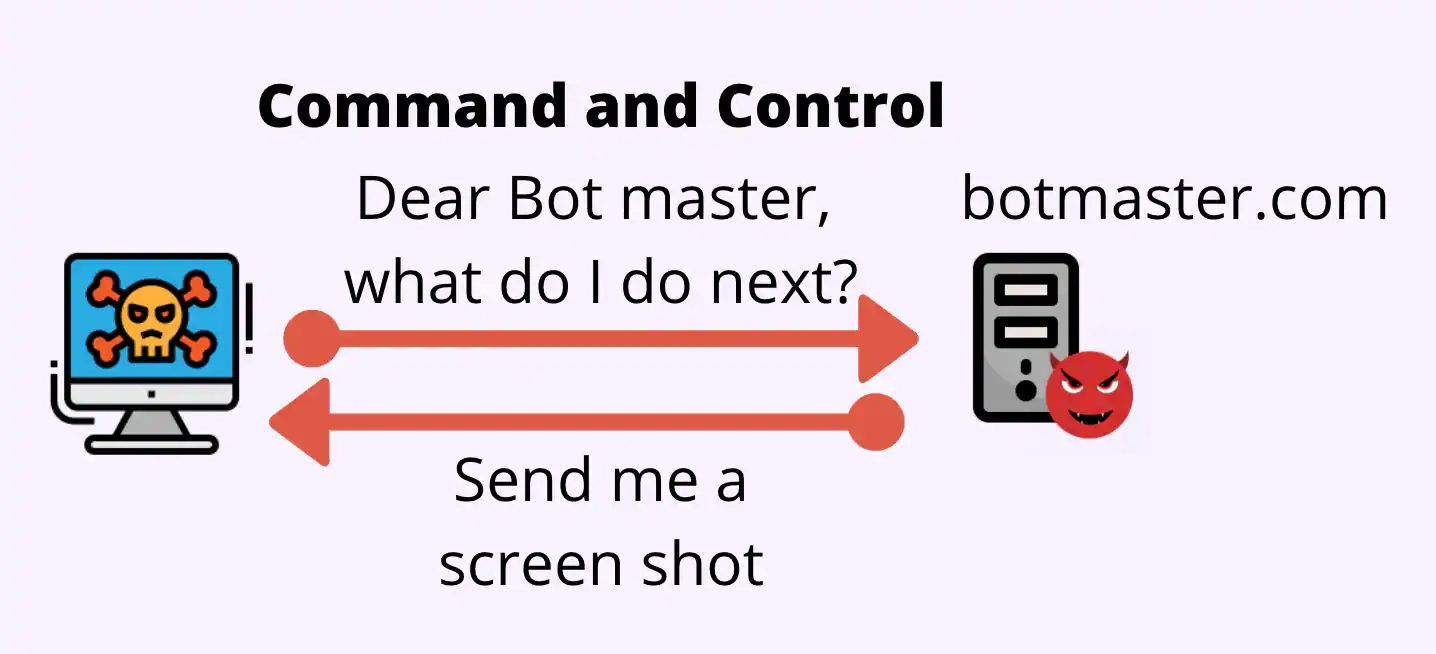
How Does DGA Malware Operate And How To Detect In A Security Operation Center - Security Investigation